
We are constantly told that the messaging platform Signal is totally secure and benevolent. While Signal may be preferable to the dominant alternatives now, there are serious concerns that organizers should discuss and further study. These include: (1) Signal’s extensive ties to the state and major corporations, (2) Signal’s extractive and anti-democratic corporate model, and (3) Signal’s technical dependence on companies like Google, Microsoft, and Amazon, which could open it up to surveillance or censorship.
Because Signal gets such glowing coverage, these concerns are rarely raised. The common wisdom that Signal is invulnerable gives many people a false sense of security.
Beyond these concerns, we should ask ourselves if the increasing use of tools like Signal harms our abilities to organize and communicate in-person, which can be not only more secure but better for building community and enabling direct action.
The Institutions and People Behind Signal
Signal emerged from Open Whisper Systems, created by cryptographer and entrepreneur Matthew Rosenfeld, better known as “Moxie Marlinspike.” There was no transparency about Open Whisper’s funding. But as previously reported, Open Whisper received funding from the US government-sponsored Open Technology Fund (OTF), which emerged from Radio Free Asia, a Cold War propaganda outlet originally created by the CIA.
Today, OTF is a place where government, academia, and corporations get together to advance US imperial interests, in part through the development and dissemination of digital technologies. It’s done under the banner of “freedom,” but in more honest moments OTF affiliates admitted that it’s really about “regime change.” Last year, for example, OTF received at least $5 million from the US government for developing “innovative methods to reach audiences inside of Cuba.” OTF has also been working with groups in Eastern Europe to create mirrors of Russian websites, with US-friendly content, that were subjected to Russian state censorship.
OTF’s Board of Directors includes people like William Schneider, a former “national security” advisor to Ronald Reagan who held positions in the Pentagon and State Department. Schneider says that his State Department responsibilities included “coordination of U.S. foreign economic and military assistance abroad”; he also listed “unconventional warfare” as one of his interests. OTF’s Board also includes Pablo Chavez, a former Microsoft and Google employee who advised genocidal Senator John McCain and is affiliated with a think tank tied to the military. OTF’s advisory council includes academics, representatives from foundations such as the Ford Foundation, and software engineers from Google.
OTF understood that Signal could be useful to US proxy groups, which is why it funded the tool.
Meredith Whittaker, current president of Signal Foundation, served on OTF’s advisory council while she was a Google employee. As a Google employee she also co-founded a think tank called AI Now, housed at New York University, and backed by Microsoft, Google, and the White House under the genocidal Obama administration. Whittaker was also an advisor to the Federal Trade Commission under the genocidal Biden administration. Whittaker is a skillful self-promoter who has been profiled in many puff pieces, contributing to the image of Signal as a noble and flawless project.
Signal Foundation’s Board of Directors reflects the same revolving door between government, elite academia, and corporations found in OTF. Its members include Jay Sullivan, an entrepreneur who worked on “privacy” for Facebook and was a general manager at Twitter. Signal’s Board also includes Katherine Maher, who was exposed for working with the State Department to promote regime change. In her work with the imperialist think tank Atlantic Council, Maher strategized about how “big tech” companies could win public trust while staying for-profit.
Signal’s Extractive Corporate Model
Signal is run by the Signal Foundation, a 501(c)3 non-profit organization. Much of what is said about Signal comes from the Foundation’s self-congratulatory posts which conceal Signal’s origins and ties to the state.
In November 2023, Signal Foundation President Meredith Whittaker and engineer Joshua Lund published a post explaining their organization’s finances. They predicted that by this year (2025) it would cost $50 million per year to run Signal, claiming that this “is very lean compared to other popular messaging apps that don’t respect your privacy.” (As others noted, they didn’t mention that Signal was made possible by state funding, and that the drop in state sponsorship left Signal scrambling for money.)
And is Signal’s model actually “lean”? The post also failed to mention Signal employees’ enormous salaries.
Signal Foundation’s 2023 tax forms show that Meredith Whittaker received an annual salary of $785,271 for working 40 hours per week (a raise of ~$588,000 from her previous year’s salary). Below are the salaries for the top 7 highest paid employees, of which the lowest paid makes ~$440,000. The salaries for just these 7 employees totaled $4.24 million, nearly 12% of Signal’s revenue that year. This is one way in which non-profit organizations turn public money (and individual donations) into private wealth. The money doesn’t go to shareholders directly, as in a for-profit corporation, but it still gets to private hands.
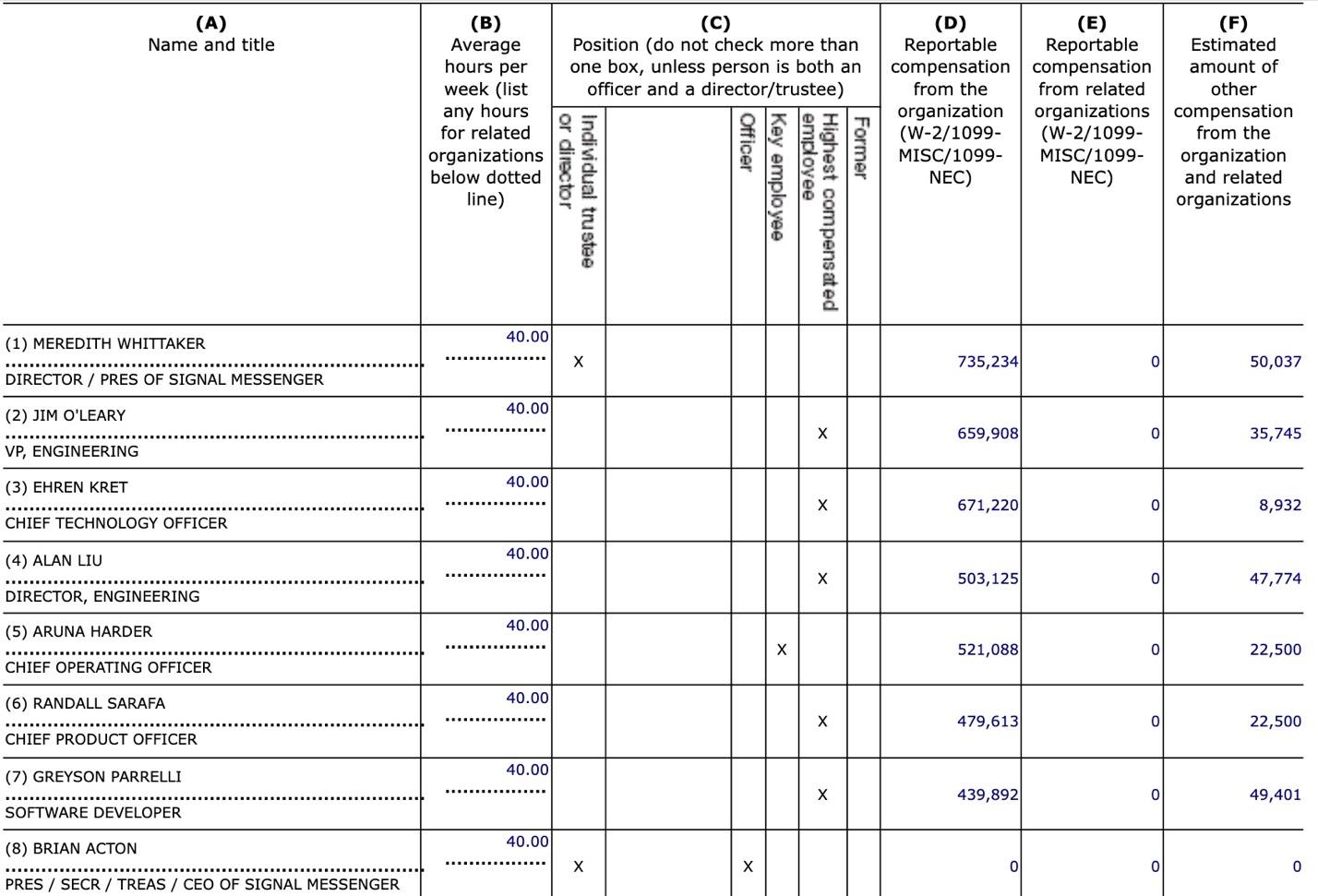
Signal Foundation’s top salaries, from its Form 990 for 2023.
Despite claiming to be “transparent,” Signal Foundation never fully disclosed its funding sources. 501(c)3 organizations don’t have to say where they got their money, but they do have to disclose money they have given to other organizations. A search in other organizations’ tax records revealed that the Musk Foundation gave $2 million to Signal Foundation in 2021 (unsurprisingly, Elon Musk tells everyone to “Use Signal”). Signal Foundation also received $16 million in 2019 from Fidelity Investments, in addition to money from the foundation of Goldman Sachs, among others.
As with every 501(c)3 organization, all decisions about Signal are made by Signal Foundation’s leadership and its board. This centralized model is unaccountable to the communities Signal claims to be serving. But it’s a good way to raise a lot of money, get tax-deductible donations from billionaires and their reputation-laundering entities, and hand out big salaries.
Signal Depends on Companies That Are Destroying the World
Recent tax forms also show the large sums Signal pays to the major companies who are destroying the world. In one year, it paid $2.29M to Amazon for hosting services, $1.86M to Google (also for hosting), and $1.38M to Microsoft (also hosting), among other companies. All these companies service the US government and military, police forces, and also the zionist entity (both before and through the ongoing genocide in Palestine). Companies like Amazon, Microsoft, and Google are also major polluters that damage the earth, waste water, and feed on exploited labor.
Does this model deserve our support? Is it sustainable? And what will happen if these companies decide they no longer want Signal as a customer?
These dependencies also make Signal vulnerable to surveillance. While Signal uses encryption, metadata about users is still stored on those companies’ servers.
This metadata could be useful to the state, which Signal has chosen to openly cooperate with. In April 2021, Signal provided information about the last time that a phone number that the authorities were interested in connected to Signal’s servers. They have also provided the dates and times in which accounts were created. In complying with these requests, Signal disclosed potentially revealing information. For instance, in August 2024, it told the state which of several phone numbers were associated with Signal accounts, and provided the associated metadata (time of creation and last login to Signal servers).
Signal’s public disclosures of these communications are filled with glib reassurances (“Signal still knows nothing about you, but inexplicably the government continues to ask”) and bad jokes about “big brother.” Yet Signal is clearly complying and giving non-trivial information, even if the details of how it is used are not yet clear.
Signal Is an Asset to the State
Signal is serving state interests, as intended by sponsors. In October 2024, at one of the New York Times’ gathering of elites, Rushan Abbas posed for a photo with Signal Foundation president Meredith Whittaker and publicly thanked Signal: “We are grateful for the secure space Signal provides for free expression, allowing human rights defenders, journalists, and dissidents to have their voices heard without fear of surveillance or censorship.” Although presented by Western media as a grassroots “human rights activist” fighting for Uyghurs, Abbas works closely with the Department of Homeland Security, State Department, and Defense Department. She was part of the Bush administration’s “War on Terror” – even working in the Guantanamo Bay prison as a translator/interrogator (while employed by the weapons developer L3 Technologies). Abbas spreads Cold War 2.0 propaganda through Radio Free Asia (once her employer), the CIA-made project that created OTF, one of Signal’s sponsors.

Signal Foundation President Meredith Whittaker (left) with state operative Rushan Abbas (right), at the 2024 Athens Democracy Forum (run in collaboration with the New York Times).
Since Signal is run by people linked to Google, it also collaborates with the company to promote US imperialist interests.
Last month, Google’s “Threat Intelligence Group” published an extensive post about a method supposedly used by Russian government-aligned actors to gain access to Signal accounts (through Signal’s “linked device” feature). Google was alarmed that the method might have been used to compromise Signal accounts belonging to Ukrainian resistance factions, which the US government and weapons industry support. The post gave a detailed account of the vulnerability, with example code, and said it has been fixed in Google’s Android app store. The post also made clear that Google and Signal are working together: “We are grateful to the team at Signal for their close partnership in investigating this activity.” (It’s not the first time Signal partnered with Google.) 
Google’s “Threat Intelligence Group” collaborating with Signal to fix a vulnerability in the app that they claim was used by Russian state-aligned agents against Ukrainian factions.
Can we imagine a similar situation where Google and Signal would rush to the aid of, say, Hamas or other Palestinian resistance groups, if these groups had uncovered a bug in Signal that would have allowed the zionist entity to snoop on them? Would Google’s “Threat Intelligence Group” publish a detailed post about the problem, with screenshots in Arabic, like it did for Ukraine? The Palestinian resistance doesn’t need the help – it built its own closed communications network, knowing well that Western digital platforms are compromised – but the hypothetical reminds us of Signal’s allegiances.
Signal’s close relationship with Google is also troubling because Google is known to engage in mass surveillance. Google, like other major companies such as Facebook, Apple, and Microsoft, collaborated with the NSA (through the PRISM program), giving the state access to its servers. The company has many connections to the government and to spy agencies like the CIA.
It’s telling that Signal could have reduced its dependence on Google, but chose not to. For example, despite requests from many users, Signal hasn’t supported the inclusion of its app on F-Droid, the open source and free software alternative to Google’s Play Store for Android. Signal’s official instructions direct everyone to Google Play Store to download the Signal app. Could this be because Signal doesn’t want to anger Google, as F-Droid goes against Google’s business interests?
A False Sense of Security
We are told that Signal is secure because it’s open source and because it uses “end-to-end encryption.” This narrative gives users a false sense of security. It overlooks the problem with the basic model used by Signal and other digital messaging platforms.
All digital activities take place in an environment – like a mobile phone or a computer – that is already highly insecure. In other words, there are many steps before and after encryption where some part of the software or hardware can be compromised. For instance, if a Signal user has notifications turned on their Android or iPhone, those messages (with their contents, by default) will be carried on Google’s or Apple’s channels; the fact that the messages were encrypted when sent is irrelevant. Similarly, Signal will by default log your audio calls (time and name of the account you spoke with) in the “Recent calls” section of your device, say an iPhone. This information will then be available to Apple and to anyone with access to data on your device, without even needing to open Signal. And if someone recorded keystrokes on a device (as the NSA has previously done), “end-to-end encryption” will provide no protection.
For “end-to-end encryption” to actually afford some privacy, there are additional precautions that must be taken to harden phones and other devices against data leaks before or after the message is encrypted. Signal is not set up by default to include these measures, some of which require more extensive technical knowledge. For Android phones, Signal is only officially supported through Googleplay, requiring most users to register their phones with Google and connect to services that regularly collect data on users and potentially share it with police.
Many people also seem to forget how easily the state can get full physical access to someone’s phone. Many also underestimate the “network effect” where one compromised device can put hundreds of people’s political activities and connections in the hands of cops.
Police are particularly interested in capturing cellphones during raids and arrests because phones carry significant amounts of data on their users, including text conversations, photographs, call logs, and lists of contacts. Police can seize phones and extract their content using tools made by the Israeli company Cellebrite. Many police departments and US agencies (including ICE and the FBI) have contracts with Cellebrite, and court cases have made clear that the company’s tools can extract data from confiscated phones.
Signal responded to a statement from Cellebrite in 2020 announcing that it had “broken” Signal’s encryption by debunking the claim: the app doesn’t protect contents of chats from being read if a phone is unlocked; apparently, Cellebrite had only succeeded in unlocking a phone with Signal on it. But it’s important for users of Signal to know that if a phone is seized by police, tools such as Cellebrite’s can be used in many cases to extract one’s Signal chats (for example, if the app can be opened or if its contents were sent through unencrypted channels such as notifications) along with the rest of the phone’s contents. Since Signal is heavily used by activists – who frequently use Signal to communicate during protests – this possibility is not remote. The threat it poses to activists should be emphasized, not minimized.
This applies to all apps, not just Signal, of course. But Signal’s great PR gives people the wrong impression that because the app uses “end-to-end encryption,” you shouldn’t worry. Any platform that projects invulnerability will be encouraging bad practice (such as bringing devices to protests and actions) and potentially creating a “honey pot.”
Questions for Our Movements
Signal’s increasing use in organizing spaces raises some crucial questions for our movements.
Is it desirable to have one central and wasteful US-based organization – connected to the state, dependent on corporations like Google and Amazon, and costing $50 million per year – run our digital communications platform?
What are the alternatives? What are different infrastructures that don’t use centralized data collection? How could these infrastructures be run in a more decentralized fashion, without the corrupt, corporate model of a non-profit? Is it possible to make this infrastructure ecologically sustainable, given the ecological harms created by large servers and data storage?
More fundamentally, we should examine the impact that Signal and similar tools have on our modes of organizing. When do the negative effects of these tools outweigh the benefits?
Like other social networking platforms, Signal is designed to connect people digitally through groups. Its architecture seems to encourage the building of large lists and networks for activists. We know of cases where chats have been built including thousands of participants. By creating an app for this, Signal has encouraged activists to communicate through – and potentially store – large networks and chats on their phones.
But phones are particularly vulnerable to surveillance, since they are easily tied to an identity and allow for the tracking of movements and interactions. Even if Signal chats are protected from remote surveillance, phones can be easily captured and seized by police if taken to protests, actions, or carried across borders. Depending on what precautions people have taken, one compromised phone can reveal entire activist networks. It’s worth emphasizing that to suppress organizing, the state doesn’t necessarily need your deepest secrets, but things like where you’ve been and who you talk to regularly.
Beyond the surveillance concerns, most of us have felt the alienating effect of the preoccupation with these apps. They can make organizing feel like a bureaucratic digital management job (while leaving a trail of “Signal Intelligence” for the authorities). An in-person meeting, when possible, is always going to be better – and often more secure – than starting yet another Signal group. The Covid pandemic has increased the alienation capitalism feeds on, including the retreat into apps, and it is essential to rebuild the culture of face-to-face meetings.
Radical action requires relationships. What ways of communicating would be best for building community, deepening our relationships to one another, and grounding us in a sense of place? Sometimes “low tech” methods such as phone trees can be better for all these things than impersonal digital messaging.
We should consider all these factors when using Signal, and critically discuss the political forces that produced this tool. We shouldn’t let the discussion be guided by technologists or the elite activists of the nonprofit-industrial complex, but by what our movements need to build the community power that can topple imperialist institutions.
Further reading about Signal
– Signal Configuration and Hardening Guide: how to make Signal more secure than the default settings.
– Mobile Phone Security for Activists and Agitators
– “Signal is a government op” (2021)
– “Signal Facing Collapse After CIA Cuts Funding” (2023)
– “Defending Privacy in the Surveillance State and Fragmenting Internet” (2024)
The post The Revolution Will Not Be Signaled appeared first on CounterPunch.org.
This content originally appeared on CounterPunch.org and was authored by The Mapping Project.
The Mapping Project | Radio Free (2025-03-07T06:54:37+00:00) The Revolution Will Not Be Signaled. Retrieved from https://www.radiofree.org/2025/03/07/the-revolution-will-not-be-signaled/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.